Ahh……. traveling through the countryside again. I’m thrifty, and don’t have unlimited cell service. I don’t want to use up all my cell phone data out here downloading movies for my kin. That’s fine, free public wireless Wi-Fi networks are everywhere. Everyone likes to get online for free. But what does “free” often mean. There are a lot of security issues with public Wi-Fi. I like to think of them as the wild-wild west. This blog will go over the big dangerous amidst many public Wi-Fi spots and how to navigate them.
 Malicious Hotspots
Malicious Hotspots
Howdy partner, welcome to free Wi-Fi. So, you’re having dinner at the Texas Steakhouse. Is the free public Wi-Fi really offered by the diner, or supplied by the guy renting an apartment next door? Perhaps someone nearby setup a rogue network to entice people to connect and snoop on your web browsing. It’s a good practice to ask an employee, or the front desk what the name of their Wi-Fi is before just jumping on the first network you find. A legitimate Wi-Fi network will be less dangerous then a malicious hotspot that is anonymously owned. You don’t want to shoot yourself in the foot, so to speak…
Wi-Fi sniffing
Just because you found the restaurant’s Wi-Fi network doesn’t make it safe either. One of the tools that hackers are using on public networks is the Pineapple Wi-Fi device. Originally developed for penetration and security testing, they can be repurposed for Man-in-the-middle attacks. After determining what websites you access, the device can thoroughly mimic preferred networks. All your information is then routed through the device. You may think you’re sending information to a HTTPS website, but it’s actually a spoofed website that the device created. What’s worse is the Pineapple can save user session and cookie information and continue masquerading as your device, long after your gone. You may need to call the local Sheriff on this network.
How do you protect yourself?
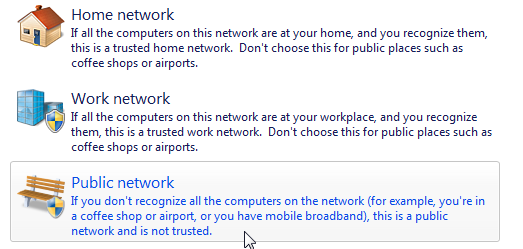
When you connect be sure you select the Public network option when connecting to public Wi-Fi, keep your computer up to date, and leave your firewall enabled. These options will protect your computer or device from being breached.
When you leave a public Wi-Fi, be sure to delete, or “forget” the network in your phone or laptop. This will keep your device from automatically reconnecting to a similar rogue network at another location.
Cautious browsing
So, we have learned how to protect your device, but what about protecting your online browsing transactions. Limiting your internet searches to informational websites that don’t pass sensitive credentials is the best practice. Logging into your online bank, even though an installed App should be avoided. What about credit card purchases? Just say no! Ok, I just want to send an email. Unless your email is encrypted (most isn’t) even email shouldn’t be checked on public Wi-Fi. Do your email servers authenticate exclusively with secure HTTPS? If you’re not 100% sure, don’t chance it. So, what about Netflix, you like watching movies don’t you? It depends…. If you can set your online accounts up with different passwords, in the event you are hacked they will only get onto that one site. Not too much at risk with a compromised Netflix account if your passwords are all unique. Plus, I get an email when another device logs on my account, so you know you can cut them off at the pass!
VPN – Circle the Wagons
What if you really need to get some work done, cellular service is not available and public Wi-Fi is your only option? Well that’s when you need to invest in a VPN service. A virtual private network (VPN) is a technology that allows you to create a secure connection over a less-secure network between your computer and the internet. This is beneficial because it guarantees an appropriate level of security and privacy to the connected systems. This is extremely useful when your Wi-Fi infrastructure may not support it. It’s like sitting inside a protective circled wagon.
If your company can setup a VPN for you that would be the best option. The next best would be a paid VPN service that’s based in the United States. Most of these run under $10 per month. Though there are many good ones outside of the States. The following VPN Services have been highly rated by CNET for 2019.
ExpressVPN
IPVanishVPN
Norton Secure VPN
Private Internet Access VPN
So, chock up and stay away from those free VPN services. Because as we just learned from this blog, nothing in life is “free”. Now head ’em up, and move ’em out

